Introduction
Like all SOAJS microservices, OAuth microservice has different layers of configuration. Local configuration, tenant-level configuration if the microservice is a multitenant one, and registry configuration. Moreover, OAuth can have a custom separate database for tokens and users.
Configuration Layers
1 - Tenant configuration
Provisioning is a configuration that all SOAJS micro-services can acquire once you turn on multi-tenant for them. Once a service becomes multi-tenant, you can provide custom tenant configuration to it at run time. If you have 2 tenants that can access the oAuth service, then the provisioned configuration for each tenant will be loaded once that tenant invokes an API in oAuth.
The below configuration is supported by the oAuth micro-service and can be configured & changed at the tenant level under the Manage Pillar.
Follow the Configuration Steps to add and update tenant configuration for OAuth
2 - Environment configuration (registry)
This configuration is on the environment level. OAuth configuration can be added from SOAJS Console.
Follow the Configuration Steps to add and update environment configuration for OAuth
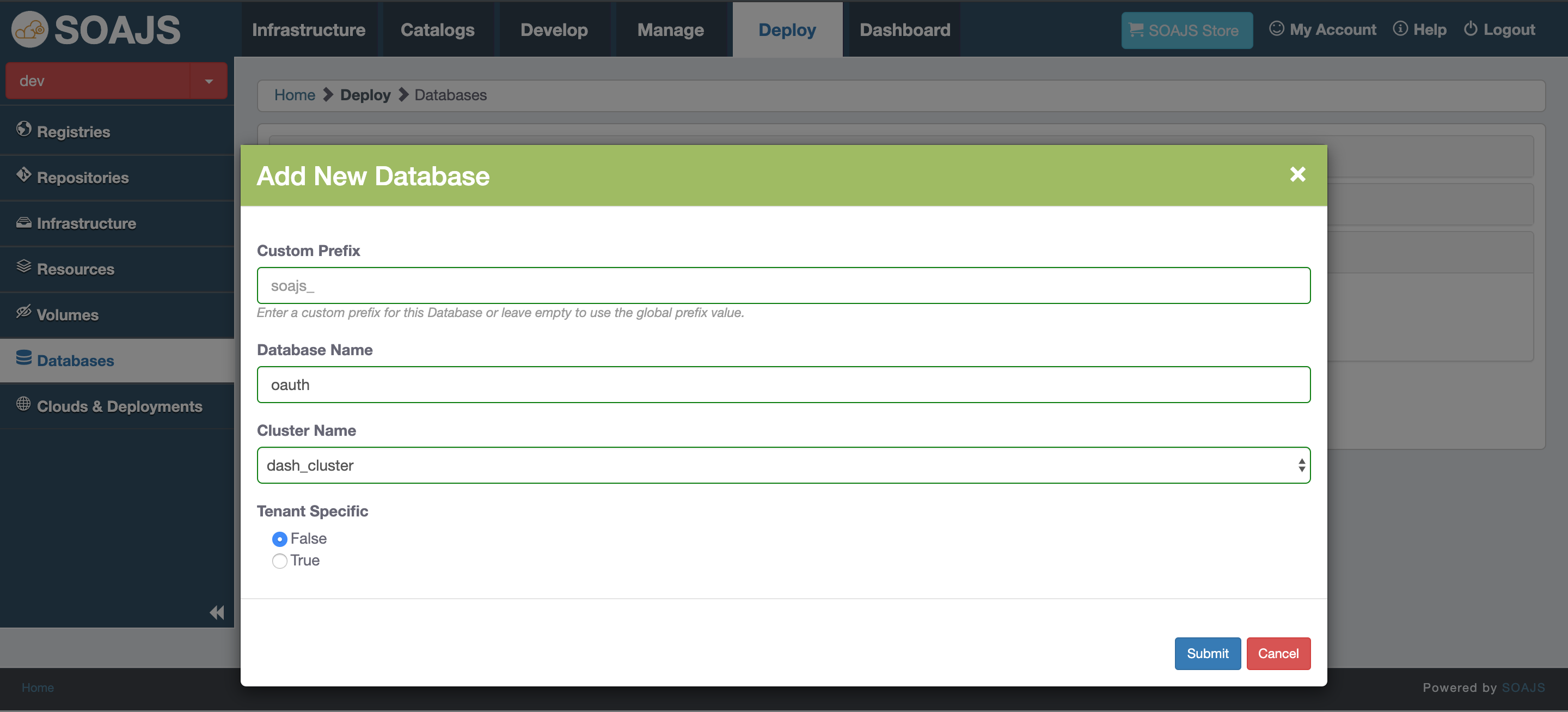
3 - Separate Database for tokens and users
OAuth can have a separate database that can be added from Deploy tab in SOAJS Console → Databases
Follow the Configuration Steps below to create a database for OAuth
The database should have the name "oauth" to be used.
4 - Tenant Key Configuration (provision)
Location
In provision - key configuration
Follow the Configuration Steps to add and update the key configuration for OAuth
Passport Login: Define application keys for passport integration. Currently supporting Github, Twitter, Facebook, and Google. Go to the link for more information and an example of the configuration.
/wiki/spaces/OAUT/pages/1433927681: Azure Active Directory Authentication Libraries allow the integration with Azure AD.
OpenAM login: SSO (Single Sign-On).
LDAP (Lightweight Directory Access Protocol) login: Active directory login.
Add Comment